
Dell Maintains Leadership as It Expands Enterprise Storage Solutions
Let’s dive into Dell storage, a key player in the infrastructure solutions group at Dell Technologies, based in Texas. Since our last discussion on Dell,
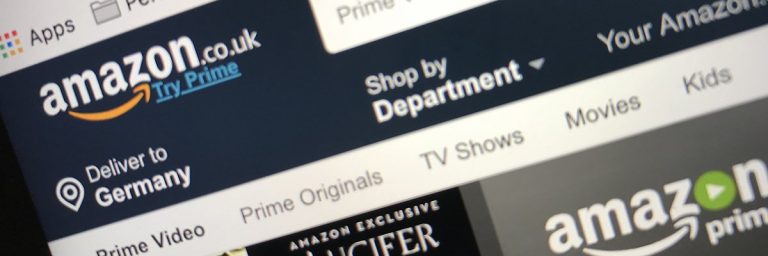
Inside Amazon UK’s Robotic-Powered Warehouse: A Behind-the-Scenes Look
The day before our visit to Amazon’s BRS2 fulfilment center in Swindon, the company made headlines by announcing its plans for drone deliveries in the
Understanding Promiscuous Mode in Networking
Promiscuous mode is a setting in networking where a network device, like a network interface card (NIC), can capture and analyze every packet that comes

IR35: Government Unveils Dual Strategy for Regulating Umbrella Companies
The government just wrapped up its consultation on tackling tax and employment rights issues linked to umbrella companies. This means we’re closer to having regulations
Understanding Computer Memory: Exploring Its Types and Functions
Memory serves as a critical hub for a computer, holding the instructions and data it needs right at its fingertips. Without memory, a computer simply

Interview with Madoc Batters: Head of Cloud and IT Security at Warner Leisure Hotels
Madoc Batters thrives on challenges. As the head of cloud and IT security at Warner Leisure Hotels, he’s taken on a significant task: spearheading the
Understanding Certificate Authorities (CAs): What They Are and Their Role
A certificate authority (CA) acts as a trusted issuer of digital certificates. These certificates authenticate the content from web servers by linking an entity with

Why Did IT Suppliers Permit Birmingham City Council to Launch Oracle?
Birmingham City Council is still grappling with issues surrounding its Oracle system as 2025 rolls in. During Monday’s budget meeting, concerns about accounting problems surfaced,
TSMC to Invest $100 Billion to Expand AI Chip Production in the U.S.
Taiwan Semiconductor Manufacturing Co. (TSMC) announced a bold plan to invest an additional $100 billion in the U.S. This move would significantly enhance the country’s
European Cloud Providers Collaborate on Data Sovereignty-Focused API
European cloud providers are being encouraged to embrace a new open-source infrastructure management API called the Sovereign Europe Cloud API (SECA). This API aims to

UK Cybersecurity Hindered by ‘Inept Political Censorship’ from the Home Office
The National Cyber Security Centre (NCSC) in Britain has quietly pulled down public guidance aimed at barristers, solicitors, and legal firms without any notice. This

MWC 2025: Accelerated Device Upgrades as AI Enhances Smartphone Experience
A new study from Assurant shows that in 2024, artificial intelligence (AI) is really becoming a big factor for people when they think about upgrading